What is SEPparser?
SEPparser is a command line tool examine artifacts from Symantec Endpoint Protection (SEP). SEPparser can be ran against a single file, directory, dead box system (write-blocked hard drive of mounted collection), or for live response.
Capabilities
- Parse settings for log files
- Parse the following log files:
- Security log
- System log
- Firewall Traffic log
- Firewall Packet log
- Application and Device Control log
- AV Management plugin log
- Daily AV logs
- Extract packets from Firewall Packet log
- Parse ccSubSDK database into csv reports
- Extract potential binary blobs from ccSubSDK
- Parse VBN files into csv reports
- Extract quarantine data to file or hex dump
- Preform hex dump of VBN for research
Using SEPparser
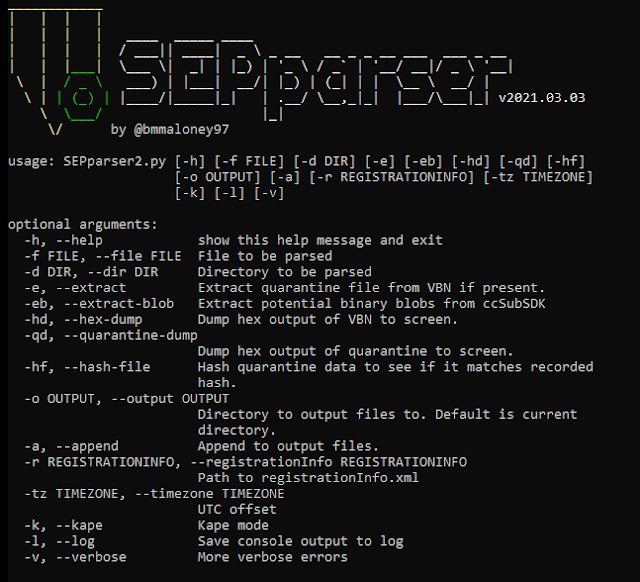
SEPparser can be ran on Windows or Linux. Running SEPparser by itself shows all the available options.
There are quite a few options, but it is straight forward to use.
Basic usage
To run SEPparser, all you need to do is point it to a file (-f) or a directory (-d) and SEPparser will take care of the rest. Output will be stored in the current directory SEPparser is ran from. This can be changed using OUTPUT (-o) option.
But what if we don't know the location of the Symantec files? The -d option can be used at the base directory and all files will be scanned from that path recursively. To speed up the process, or if we are using a script, we can use KAPE mode (-k) in conjunction with -d. What this does is SEPparser will only scan files in locations where SEP data is stored instead of every file.
If we want to append data to output files that SEPparser already created, the append (-a) option can be used.
Once SEPparser is finished a series of csv files will be created.
Time Zones
Some of the time stamps in SEP's data are in UTC and others are recorded in the time zone set on the device they came from. There are a couple of ways to get all the time stamps to be in UTC.
- If the registrationInfo.xml file is found during the scan; the offset will be automatically applied.
- The -r option can be used to point to the location of the registrationInfo.xml file so the offset can be automatically applied.
- The -tz option can be used to manually enter a time zone offset.
Logging
SEPparser has a logging feature (-l) that can be used to save the console output to a log file. This can be useful to check for errors during parsing. If an error occurred, the -v option can be used to get a more verbose output of what went wrong.
Quarantine Files (VBN)
When it comes to quarantine files, SEPparser has some additional features that can be useful.
SEPparser has the ability to extract (-e) the quarantined data or it can dump the data to the console in hex format with the -qd option.
SEPparser can also produce a hex dump of the VBN itself. While SEPparser does a rather excellent job of parsing VBN's into the csv report, there is still data that it cannot. There are some parts of the VBN format that are unknown. The hex dump can help researchers to understand and figure out what these unknown parts of the file format mean.
SEPparser also contains hash-file (-hf) option. This can be used when parsing VBN files for reports. Because there can be extra data in the VBN file, the hash reported is not always the hash of the actual file. With the -hf option, SEPparser will record the MD5, SHA1, and SHA256 of the actual quarantined data.
ccSubSDK Database
SEPparser has an extract-blob (-eb) option that can be used when parsing the ccSubSDK database. With this option enabled, SEPparser will extract anything that could be an executable contained in the ccSubSDK database.
Packets
SEPparser has one more trick up its sleeve. When parsing the raw.log (packet log), SEPparser will extract the packets from the log into a text file. This text file can then be loaded into a tool, like Wireshark, to examine the packets. SEP only captures the headers and not the data associated with it.