We'll start out by firing up ProcDOT and generate our graph.Looking at the graph, I have eight different server nodes (yours might be different). Make note of the servers listed.
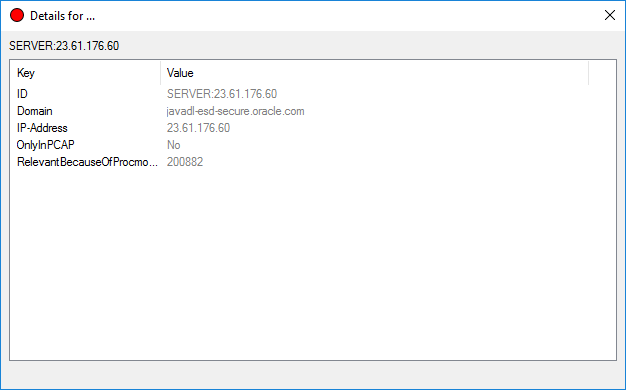
Right click on one of the server nodes and select details.
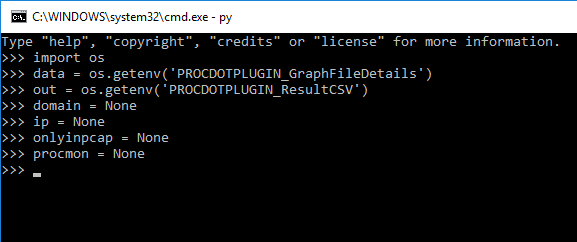
From here, drop into a python shell by typing python and hit enter.
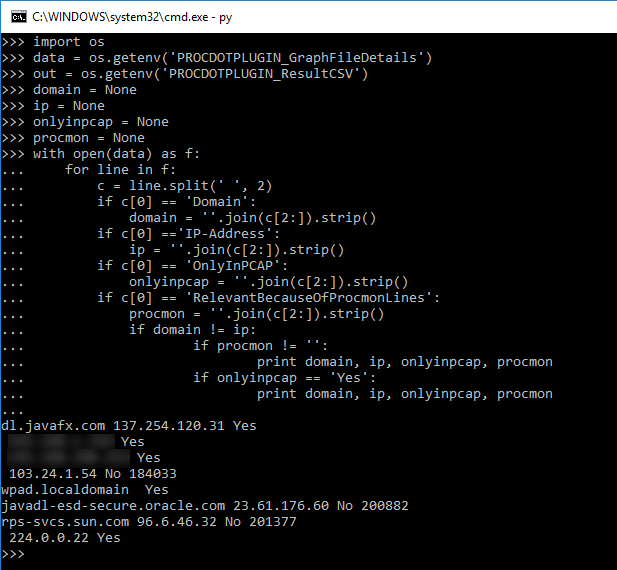
We will need to import os into the python shell so we can get our ProcDOT variables and assign them in our plugin.After that, we will create some variables for our key data we are after.
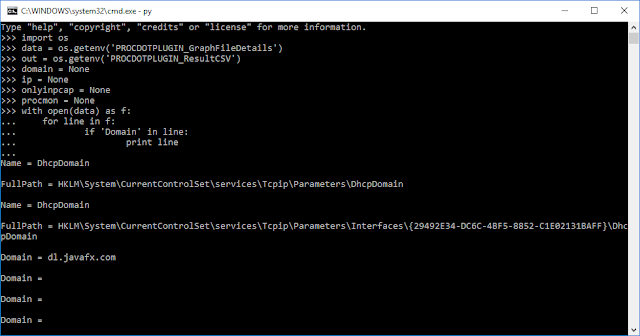
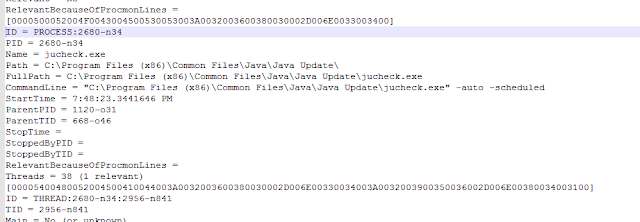
Next we will open the details file in python and search it, line by line, for the Domain keys. For every hit we get on Domain, we'll have python print it out.
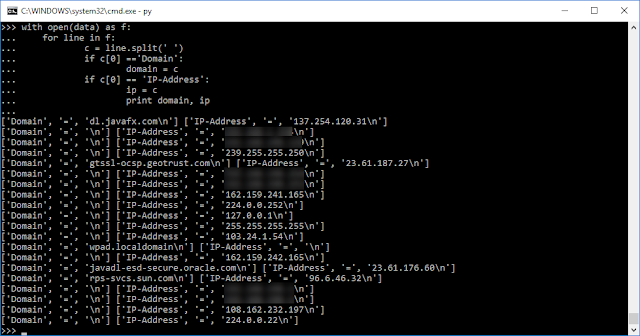
Hmmm. Looks like we are getting back the Domain key and then some. Looking at the format of the file, we can split the lines apart with a space. This will split the line into three parts. We can go back and search the first part for Domain and try it again.
Now we are getting somewhere! But there is another problem. Not every server node has a Domain tied to it. If we look back, we can see that we can also search for the IP-Address. I we assign these to our variables, we can print these together.
So, looking at the output, we can see that the server nodes that are in the graph also contain an entry in the RelevantBecauseOfProcmonLines key. And the server nodes that are marked yes in the OnlyInPCAP key are also in the graph. Lets parse this out a little more and strip out what we don't before we write our actual plugin. We'll reset some of our variables and finish this up.
Nice! We can now write our plugin. In order for our output to come out right, we will have to refer to the ProcDOT documentation to make sure the result csv is properly formatted.
So looking at this, the first line of the file contains the headers surrounded in quotation marks and separated by commas. The next line is the column widths, then finally our data. We are only going to have headers for the Domain and the IP-Address. We'll add some style by marking the server nodes that are only in the pcap with blue lettering. With our plan in place, we can create the plugin and the pdp file.
server.pdp
Name = server
Author = <your name>
Description = Open cmd prompt from ProcDOT's Main Menu
Version = 1
Type = MainMenuItem
Architecture = WindowsBatchScript
File = server.bat
Priority = 9
RunHidden = 1
RunExclusively = 1
CanOverrideOtherPlugins = 0
CanOverrideProcdot = 0
server.bat
@setlocal enabledelayedexpansion && python -x "%~f0" %* & exit /b !ERRORLEVEL!
import os
def main():
data = os.getenv('PROCDOTPLUGIN_GraphFileDetails')
out = os.getenv('PROCDOTPLUGIN_ResultCSV')
outfile =open(out, 'w')
domain = None
ip = None
onlyinpcap = None
procmon = None
outfile.write('"Domain","IP-Address"\n')
outfile.write('"*","*"\n')
with open(data) as f:
for line in f:
c = line.split(' ', 2)
if c[0] == 'Domain':
domain = ''.join(c[2:]).strip()
if c[0] =='IP-Address':
ip = ''.join(c[2:]).strip()
if c[0] == 'OnlyInPCAP':
onlyinpcap = ''.join(c[2:]).strip()
if c[0] == 'RelevantBecauseOfProcmonLines':
procmon = ''.join(c[2:]).strip()
if domain != ip:
if procmon != '':
outfile.write('"' +domain + '","' + ip + '"\n')
if onlyinpcap == 'Yes':
outfile.write('{{color:blue}}' + '"' + domain + '","' + ip + '"\n')
if __name__ == '__main__':
main()
Save these to your plugin folder restart ProcDOT and generate a graph. From the Plugin menu, select server and you should see the results.
Success! We made a plugin to display all the servers in the graph. Before we conclude, the cmd plugin can be used to troubleshoot our plugin. Lets say we made a typo in our plugin and no results were returned. We can't see any of the error messages to see what happened. To test this out, open the server.bat file and change domain = None to dmain = None and save the file. If we run the server plugin again our results come back empty.
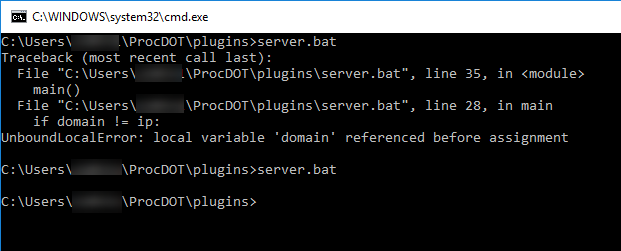
We don't know why because we cannot see the errors. Close out the results and launch the cmd plugin from the Plugin menu. From this command prompt, we can run the server plugin manually. Type server.bat in the command prompt and hit enter.
From the output, we can see the error UnboundLocalError: local variable 'domain' referenced before assignment. If we edit server.bat back to domain = None and save again, we can run the plugin manually and see that there are no more errors. Pretty neat!
Our simple cmd plugin turns out to be rather useful for writing and troubleshooting plugins. Now that we have a way to better develop our plugins, we will create a plugin for the context menu in the next tutorial.