Pictures are worth a thousand words. Enjoy!!!!
HKLM\SYSTEM\CurrentControlSet\Enum\USBSTOR
HKLM\SYSTEM\CurrentControlSet\Enum\USB
HKLM\SYSTEM\MountedDevices
Monday, August 21, 2017
Thursday, August 17, 2017
Comparing Packet Captures to Procmon Traces
Trying to match Procmon entries to a packet capture can seem frustrating at first. There are two things that stand out to me in the Procmon entries:
1. The times are off ever so slightly compared to the packet capture
2. There is not an entry for every packet in Procmons output
We can solve this problem by looking at the times and lengths of the packets. To make things a little easier to read, I'll use the csv output from Procmon and use windump to filer the packets. The first thing I do is filter the Operation column so it contains tcp events.
And then I filter the Path column by the IP address I am trying to match.
The csv should look something like this:
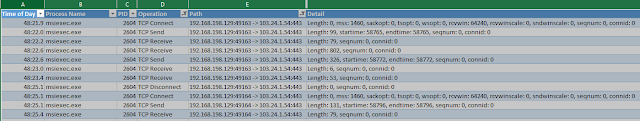
Now that the Procmon csv is filtered, I can run Windump and filter on the IP in question. Piping the output to a file will make this easier. To do this, run the following command:
WinDump.exe -n -p -r malware.pcap host 103.24.1.54 > output.txt
The resulting file should look something like this:
The number in the parentheses is the length of the packet. Once we start matching the approximate times and the length of the packets, the picture becomes a lot clearer.
I hope this helps anyone trying to compare packet captures to Procmon output.
1. The times are off ever so slightly compared to the packet capture
2. There is not an entry for every packet in Procmons output
We can solve this problem by looking at the times and lengths of the packets. To make things a little easier to read, I'll use the csv output from Procmon and use windump to filer the packets. The first thing I do is filter the Operation column so it contains tcp events.
And then I filter the Path column by the IP address I am trying to match.
The csv should look something like this:

Now that the Procmon csv is filtered, I can run Windump and filter on the IP in question. Piping the output to a file will make this easier. To do this, run the following command:
WinDump.exe -n -p -r malware.pcap host 103.24.1.54 > output.txt
The resulting file should look something like this:
The number in the parentheses is the length of the packet. Once we start matching the approximate times and the length of the packets, the picture becomes a lot clearer.
I hope this helps anyone trying to compare packet captures to Procmon output.
Subscribe to:
Comments (Atom)







